Disinformation isn’t just a social engineering attack, it’s an buffer overflow attack of the mind.
Most people may not be familiar with an information security vulnerability called a buffer overflow. Here’s a small example:
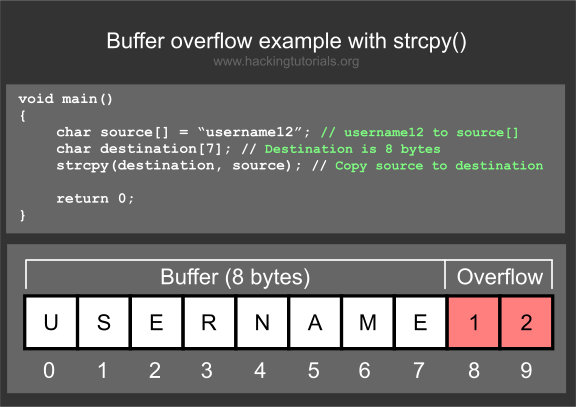
Buffer Overflow attacks work when a program needs to accept input from the user (think of a program that asks for your username, like the example above). The issue is that the programmer uses a function like strcpy() where the size of the destination is not specified. The problem here is two fold:
1. If you throw enough data into this input area, it can crash, resulting in a Denial of Service condition.
2. If you craft a specialized request, taking into account memory allocations, you can trick the program into running almost any code you want it to run.
Continue reading