WestWild Walkthrough
This is a walkthrough of the beginner-level CTF machine “WestWild” on Vulnhub.
****Spoiler Alert**** ****Spoiler Alert****
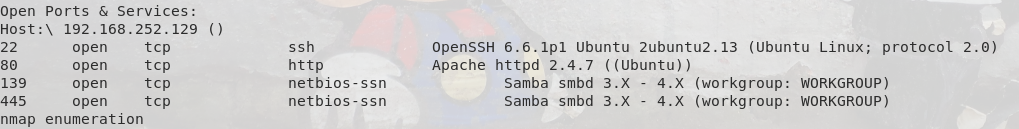
So there is an obvious web page here after bootup, but it’s a red herring and we’ll rely on our trusty nmap scan:
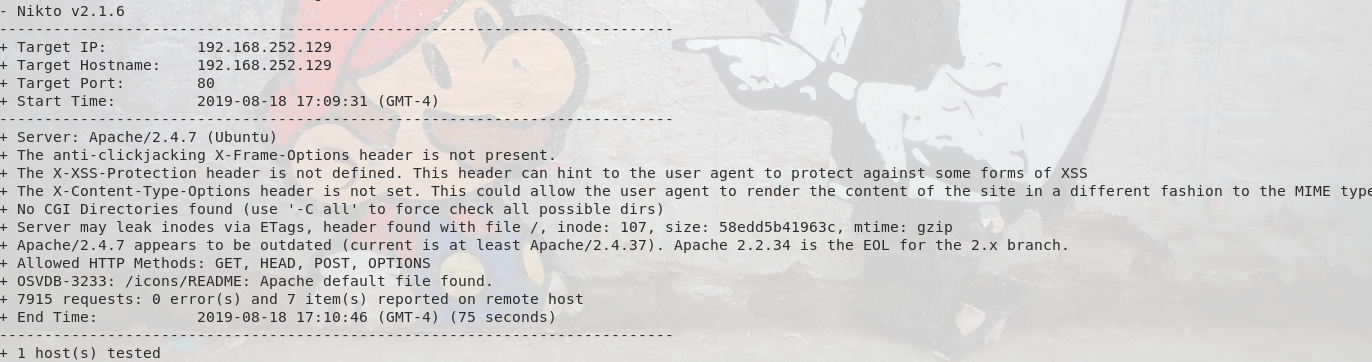
Ok, let’s see if nikto turns up anything for HTTP:
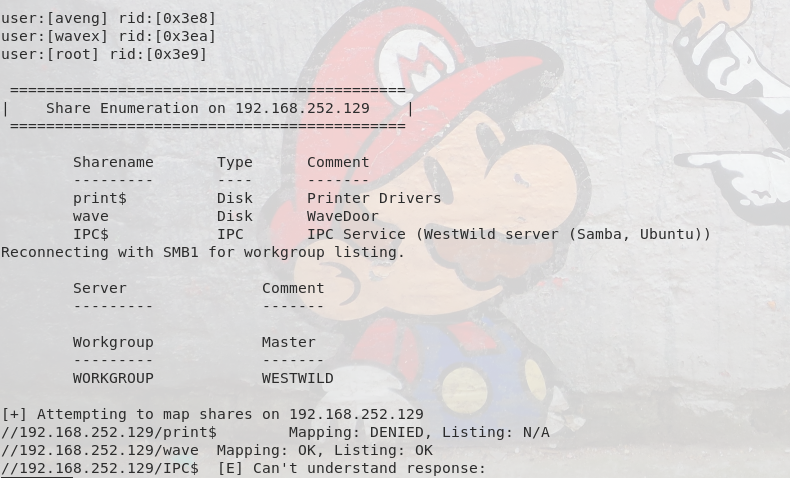
Doesn’t look like anything special to me. Let’s take a look at Samba and see if enum4linux turns up anything interesting:
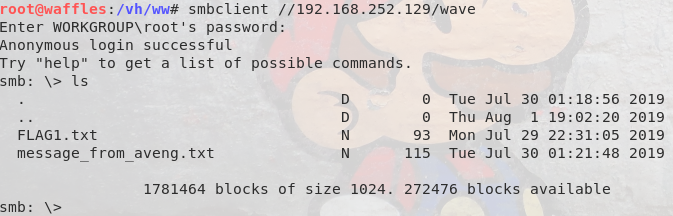
Great! Looks like we have 2 users (wavex & aveng) as well as a share we should be able to access (“wave”). Let’s see if we can access it and get any more information there:
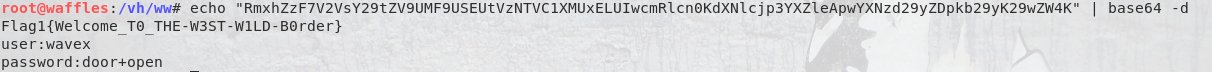
Bingo! We have our first flag & a clue. The clue was a message from aveng to wavex saying that he forgot his password and could wavex reset. Ok, so wavex has those perms and this should point to the wavex user being the gateway to the aveng user. The flag file also looked a little odd. Too long to be a hash itself and so must be encoded, so I ran it past a Base64 decode:
So now we have our login for the wavex user. After logging in though I didn’t have any sudo privs and so started a generic privEsc file search thorugh SUIDs, GUIDs, and finally writable files: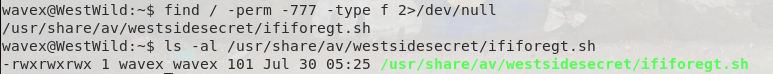
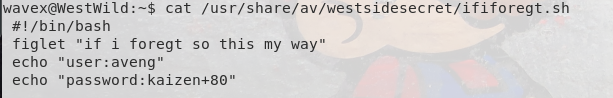
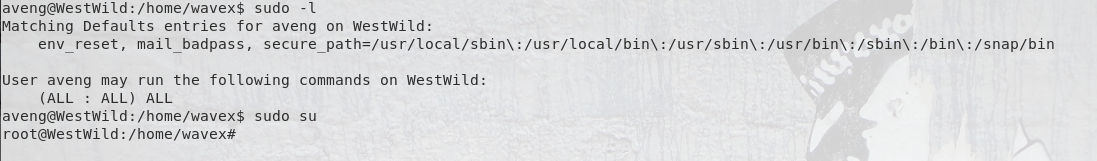
Ok, so it looks like we have a file specifically for aveng when the user forgets their password, that includes their password. Let’s switch users and check their permissions:
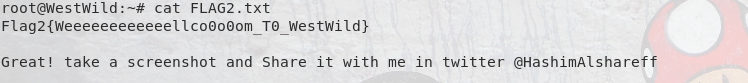
I would normally show permission levels with id but I actually forgot that step once I saw the “ALL” command access from sudo. Let’s switch to the root directory and grab the final flag: